Discover the Solution
A unified, high-performance AI platform engineered for modern cybersecurity operations.
From ethical offensive assessments to advanced defensive analytics, the platform tailors its behavior to your mission—vulnerability discovery, threat hunting, IR workflows, and competitive challenges.
Select your profile. Define your mission. The AI adapts.
Launch AI-driven security operations in three simple steps.
Securely attach your environment via SSH. Use your own infrastructure or leverage the default BackBox Linux setup with a complete security toolchain.
Choose the AI profile that best aligns with your mission—whether offensive testing, defensive operations, or analytical research.
Describe your objective. The AI responds with expert guidance or creates a structured plan for autonomous execution—always requiring your approval.
Core features designed for teams that demand speed, reliability, and operational integrity.
Expert personas tailored to key security functions—Penetration Tester, Threat Analyst, and more. Each profile dynamically adjusts its behavior from assistant-level guidance to structured autonomous workflows, depending on the complexity of your request.
Backed by advanced language models with automatic task-based model selection. The platform evaluates each mission—whether reconnaissance or deep multi-step reasoning—to deliver optimal speed, accuracy, and reliability.
Connect your environment via SSH and let the AI operate directly within your controlled infrastructure. Use your own systems or the pre-configured BackBox Linux environment. Real commands. Real execution. Fully contained.
Run multiple assessments simultaneously. Switch contexts instantly, compare results, and maintain persistent insights across profiles—synchronized and available across devices.
The AI provides transparent plans and requires confirmation for critical or impactful actions. Safety gates prevent unintended execution, ensuring alignment with internal policies and compliance standards.
The platform retains context across sessions—remembering findings, executed actions, and methodologies—allowing you to resume complex assessments without repeating information.
Designed for flexibility, clarity, and seamless workflow transitions.
"Explain how SQL injection applies in this scenario."
Expert knowledge, procedural guidance, and rapid technical insight—no execution.
"Exploit this vulnerable application and get shell access"
Autonomous workflows with transparent plans and required confirmations before impactful steps.
"Review these SIEM alerts, then prepare recommended mitigation actions."
Blend analysis and automation in a single, fluid conversation.
Specialized personas designed for high-impact cybersecurity operations.
Enterprise-ready offensive intelligence. Combine expert consultation with autonomous workflows for penetration testing, vulnerability research, attack-chain validation, and structured CTF problem-solving.
A scalable, analytical framework for defensive teams. Automate triage, correlate threat intelligence, and accelerate incident response with clear, explainable reasoning.
A unified, high-performance AI platform engineered for modern cybersecurity operations.
Supporting the professionals who safeguard modern organizations.
Execute structured offensive engagements with improved speed, depth, and operational efficiency.
Investigate incidents, correlate evidence, and map adversary behaviors with enhanced analytical precision.
Conduct on-chain investigations, trace transactions, and uncover patterns to support blockchain forensics and threat intelligence.
Need specialized workflows or enterprise integrations? We provide tailored solutions.
Xfenser AI provides an intuitive interface to manage and interact with key components of your cybersecurity workflow.
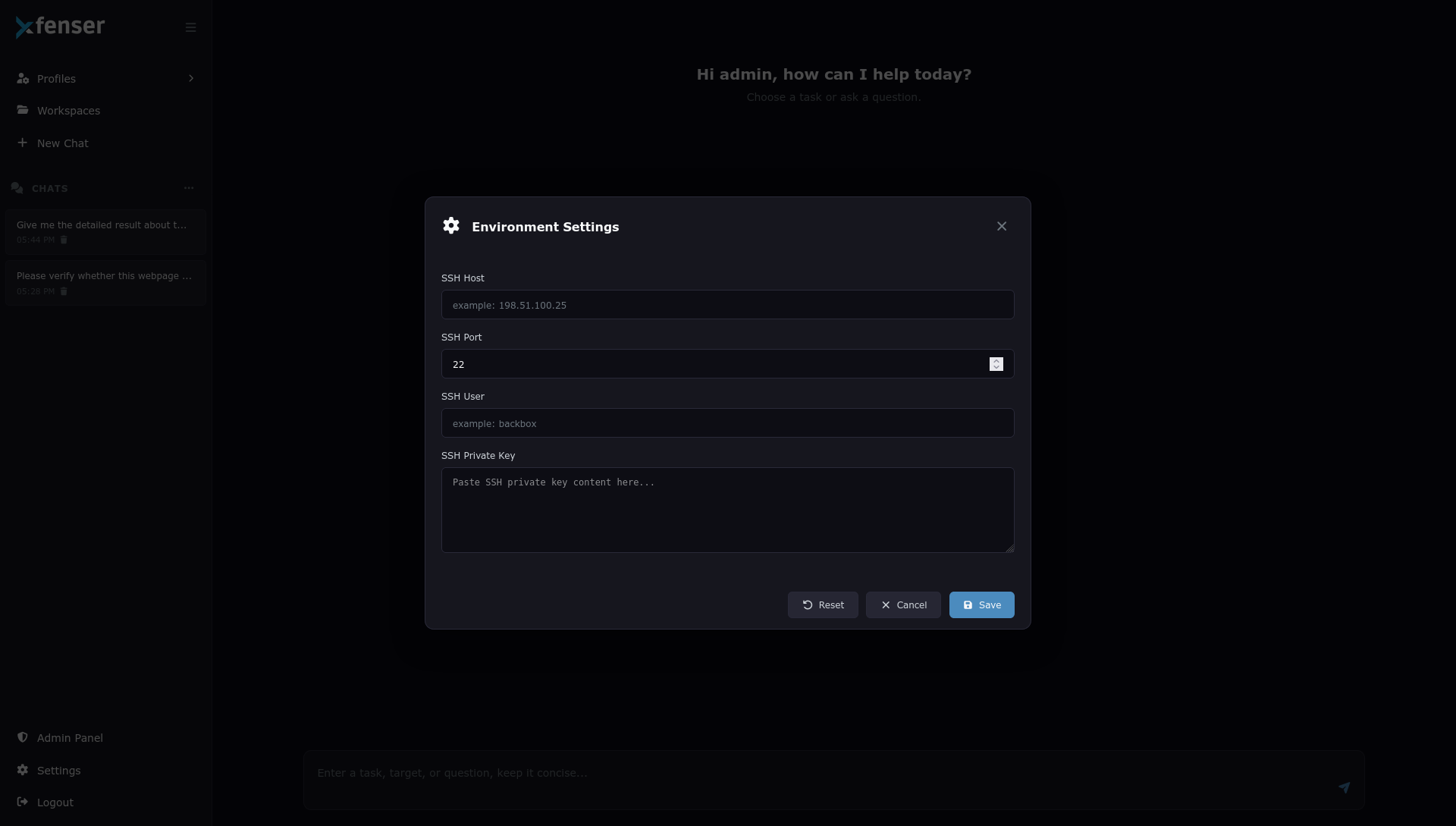
Configure secure SSH access within seconds.
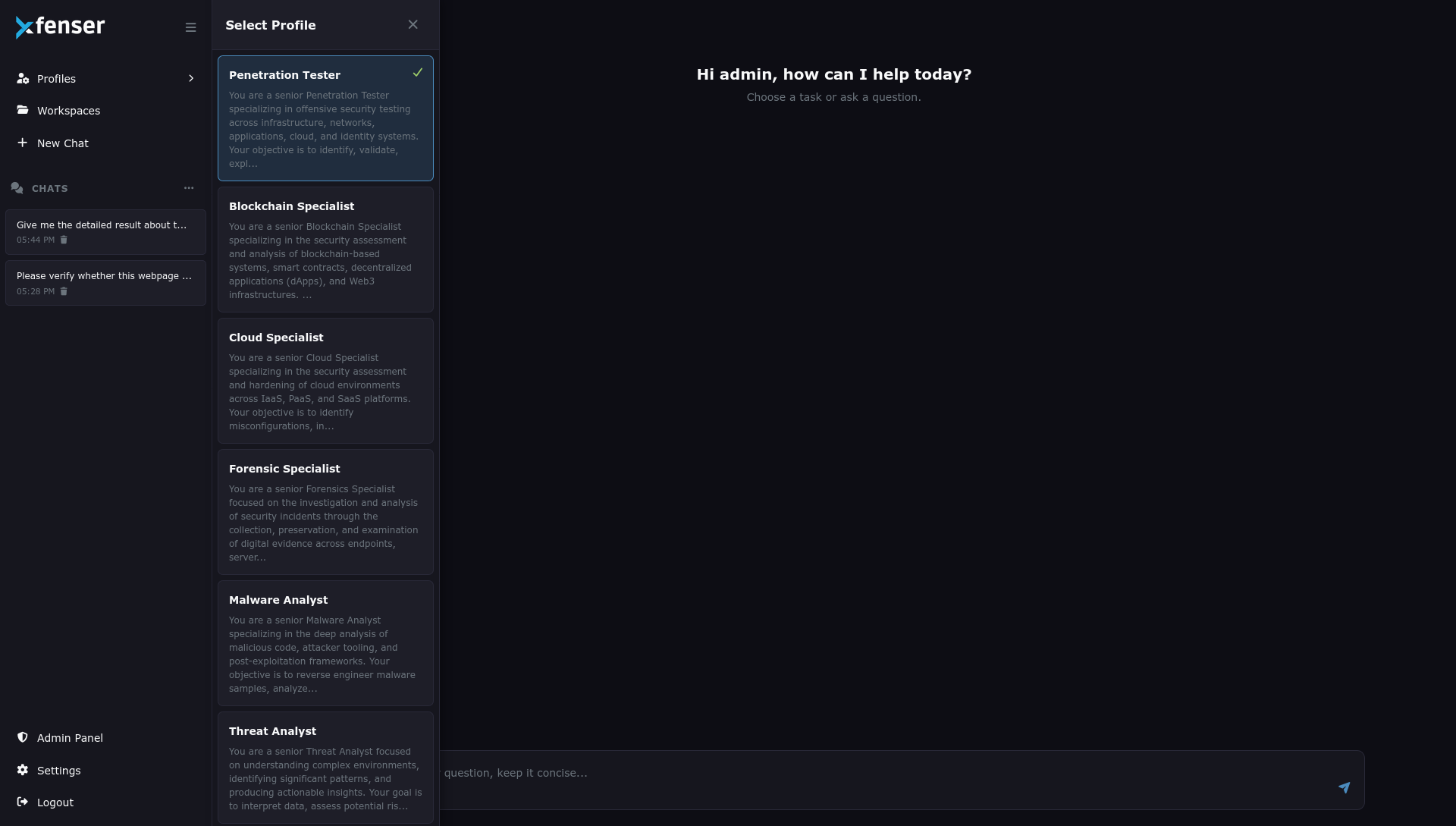
Select the AI agent aligned with your mission.
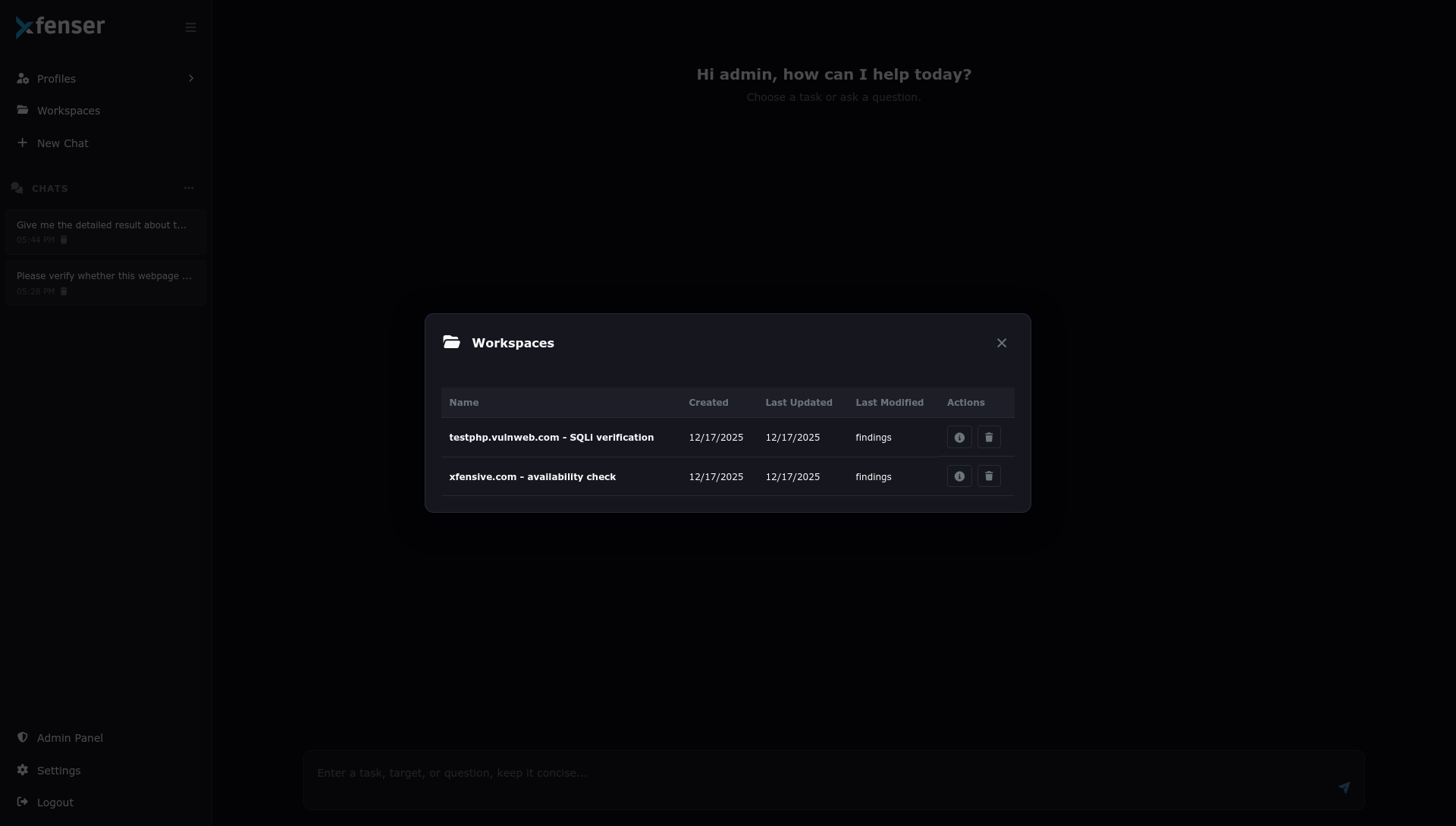
View, manage, and delete workspaces effortlessly for streamlined operations.
Empower your team with adaptive AI designed for real-world cybersecurity challenges.